customer trust starts with cyber trust.
earning customer trust in your online services takes time.
losing it takes only one vulnerability.
Manage your risks. Protect your reputation. Discover weaknesses before they are exploited. Simulate real-world attacks and stay secure every day—either through our intuitive platform or via our fully managed service.
What’s your approach? Don’t just react to disruptions. Prioritize long-term resilience and system reliability to keep your customers' data safe.
Resilience over reaction.
Treating cybersecurity as a go-to-market advantage is the key to winning customer trust in the age of AI.


PREVENT COSTLY FLAWS.
SECURITY BY DESIGN.
Professional Threat Modelling and Vulnerability Monitoring made accessible.
Get the power of enterprise-grade Threat Modeling methodology without the enterprise price tag. Our solution provides a formalised, step-by-step workflow, and AI-supported attack simulation and mitigation advisory based on established frameworks and industry-standards like CWE, CAPEC, CVE and OWASP.
Move from unclear reality to a methodical, fully documented approach, giving your team the control needed to protect critical revenue streams.
€ 395
per month
...
...
CONTINUE
This has offloaded tedious but important work that otherwise would have been neglected. We also discovered a design miss that had totally gone under the radar.
- B. Allotey, Commercial Bank, Italy
The design of our online service was verified ok, which is good, but the vulnerability monitoring is what truly adds value. Love the riskogram!
- H. David, Singapore
By leveraging your service, we've learnt to proactively defend our online assets, maintain customer trust, and stay ahead of emerging cyber threats at a very reasonable cost.
- Customer, UK
SIGN UP TODAY
BENEFITS
Comprehensive Threat and Vulnerability Control
▶ Identify and Mitigate Risks: Our solution provides a thorough analysis of potential threats, design weaknesses, and other vulnerabilities, helping you identify and mitigate risks before they become critical issues.
▶ Monitor Vulnerabilities: Stay ahead of threats with daily vulnerability reporting, ensuring your systems are always protected.
Cost-Effective Cybersecurity
▶ Affordable Pricing: Get enterprise-level cybersecurity at a fraction of the cost.
▶ No-Brainer ROI: One month's subscription fee is less than an hour's fee of a seasoned security consultant.
Educational Resources
▶ Learn While Protecting: Become proficient enough to manage your own cybersecurity.
▶ In-App Advisory and YouTube Channel: Access educational resources directly within the app and through our YouTube channel.
User-Friendly Interface
▶ Intuitive Dashboard: Our user-friendly dashboard makes it easy for IT managers and developers to navigate and understand security insights.
DISCOVER THE INSIDE
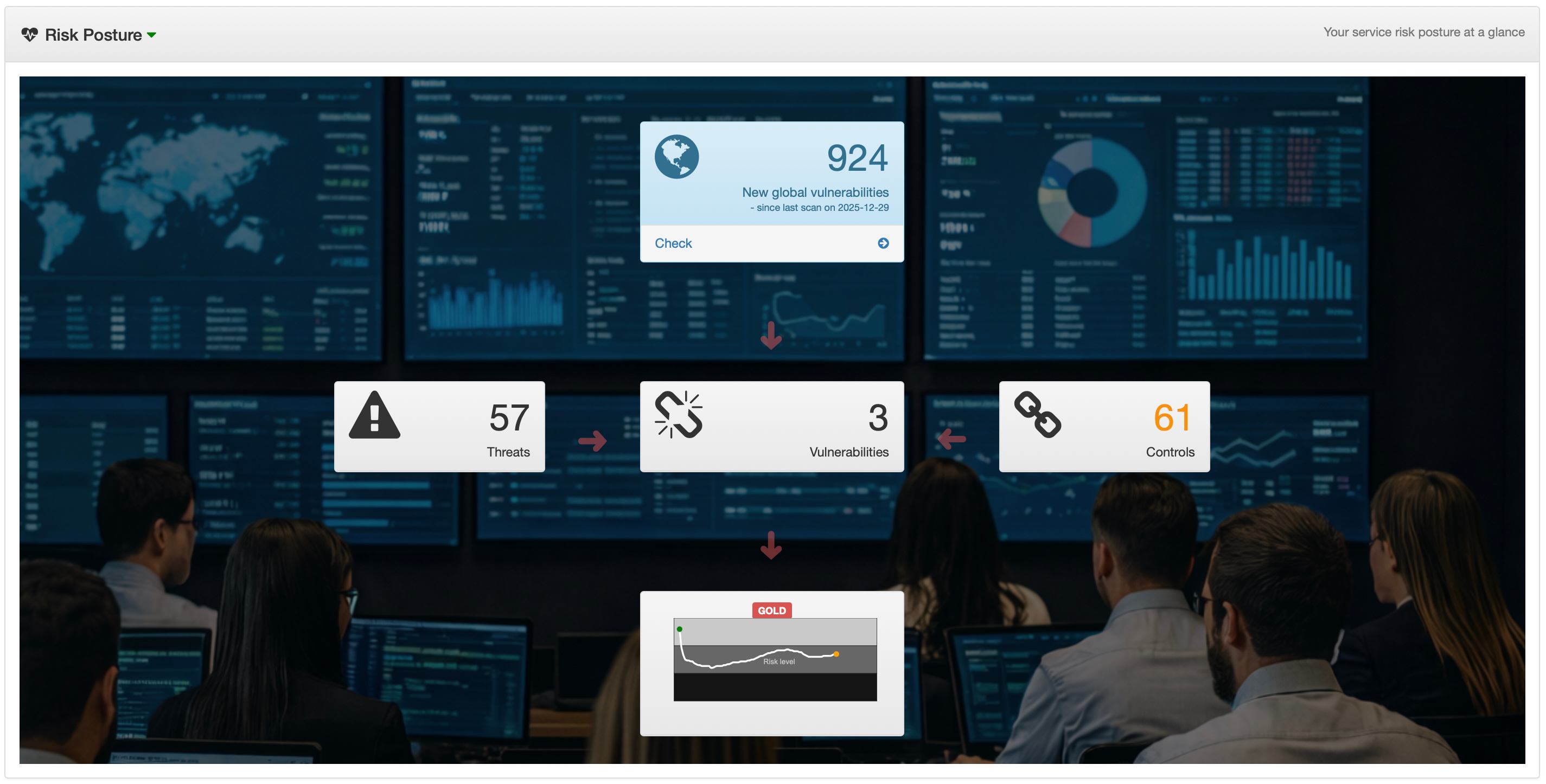
Get inspired by your increasing maturity level
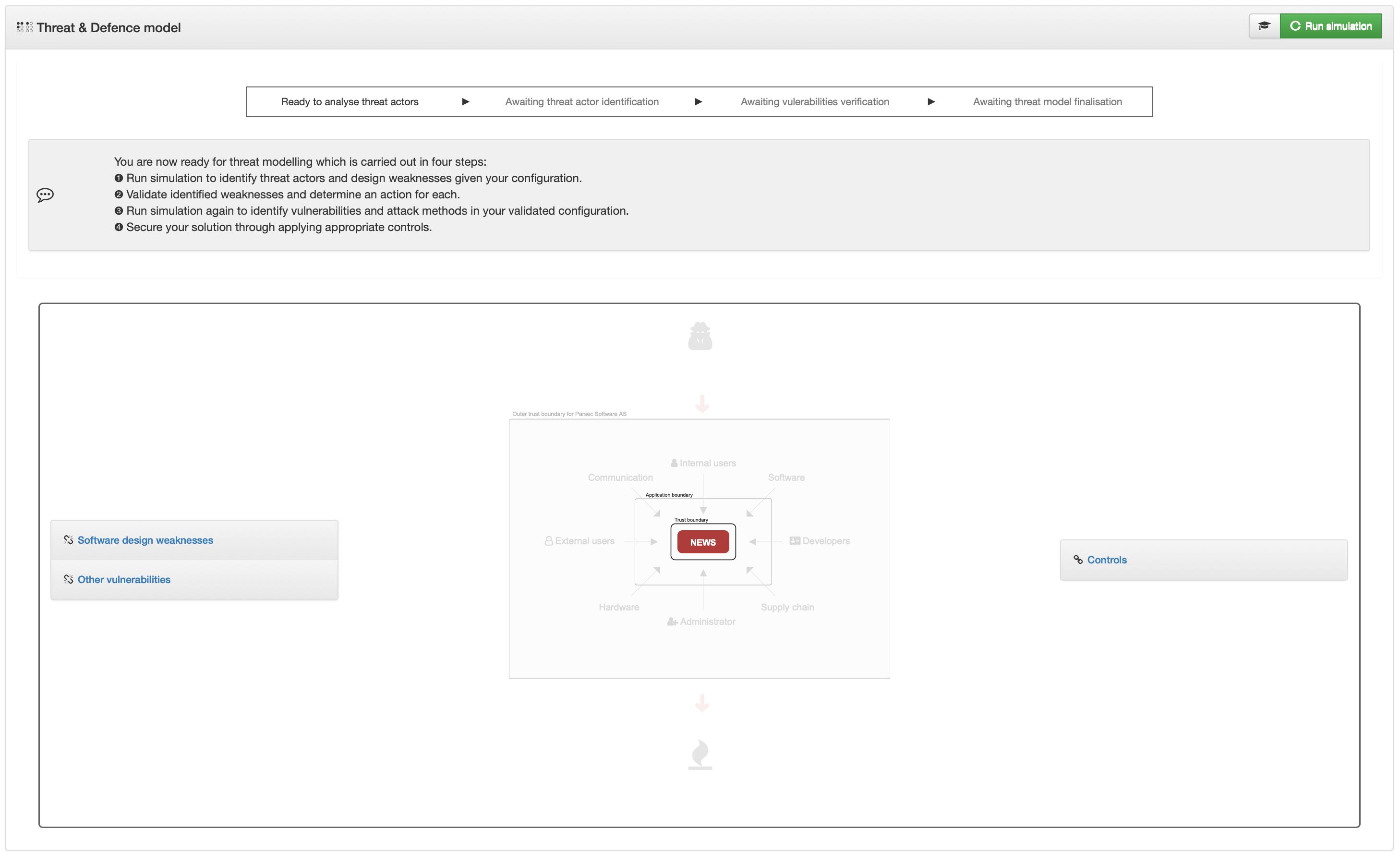
Get inspired by your increasing maturity level in keeping the business secure. With that in mind, cyberriskguru is designed to unlock supporting features as you grow. Above shows the Risk Posture which unlocks at 50% maturity. Here is how the various maturity and related screenshots looks like:
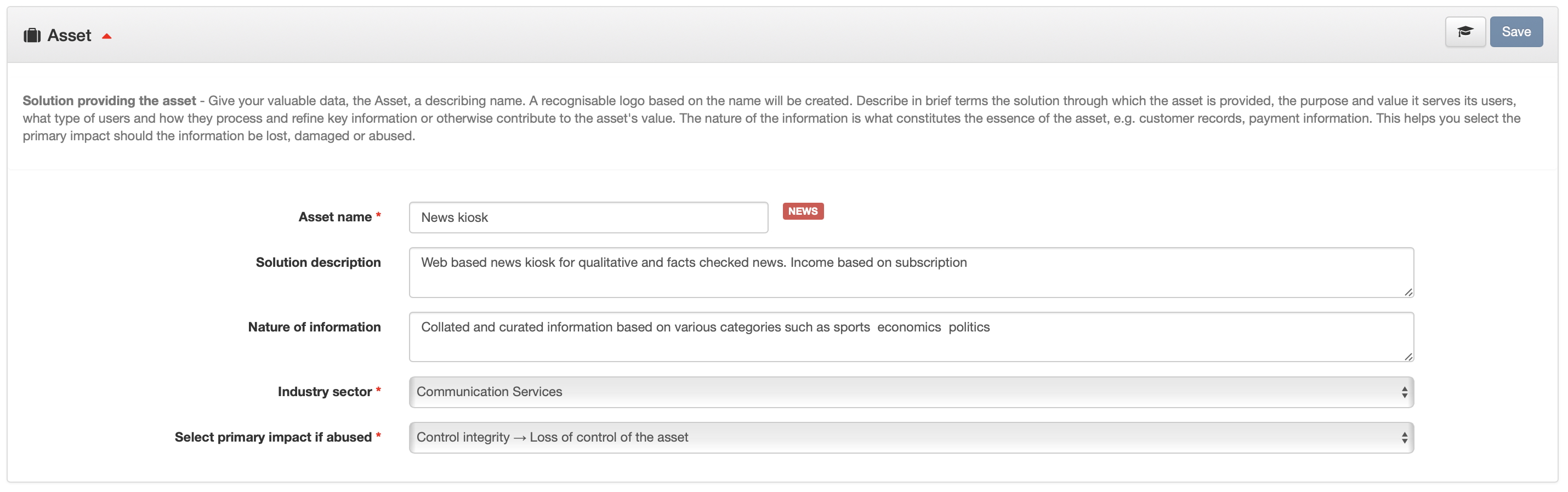
10%
Completed configuration of your Asset - the crown jewels you want to protect
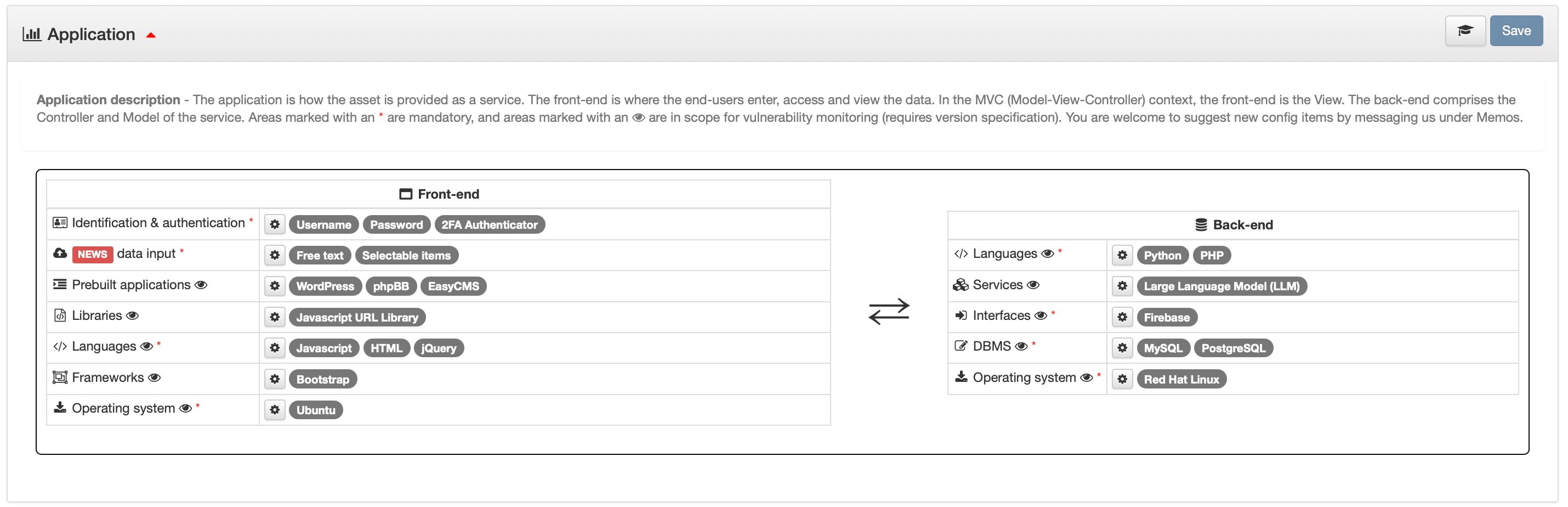
20%
Completed configuration of the Application the is providing your Asset as a servie
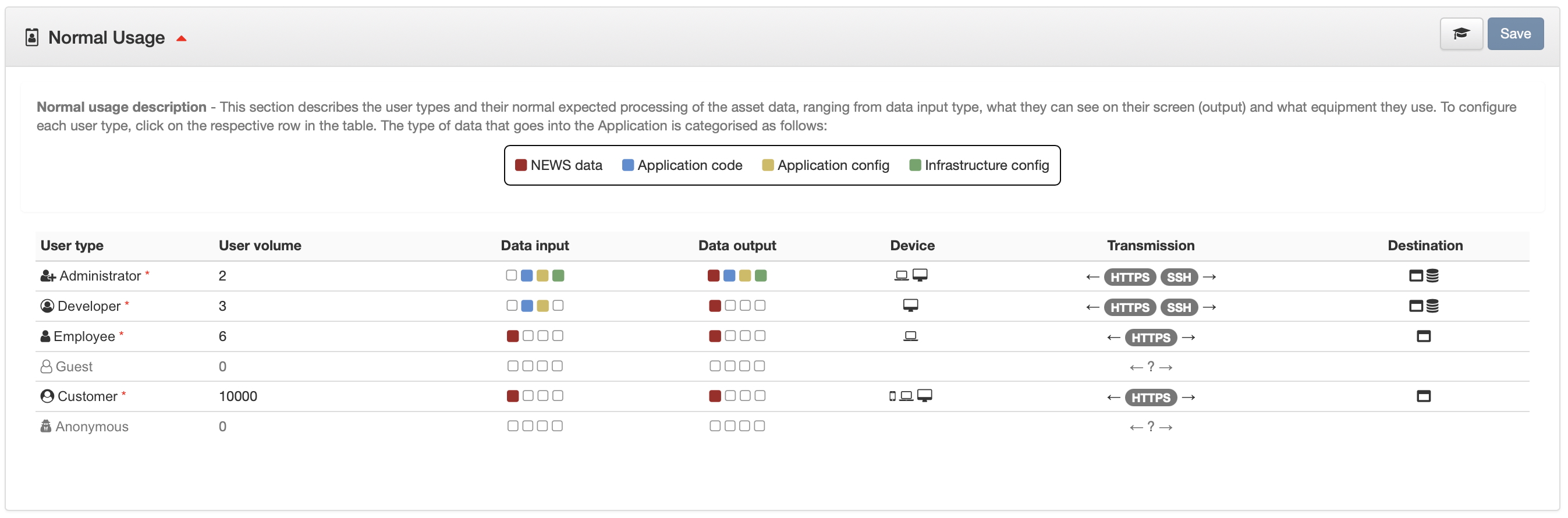
30%
Completed configuration of the Normal Usage
40%
All configuration completed, ready for attack simulation
Riskogram unlocked illustrating prevalent risk vectors toward your service
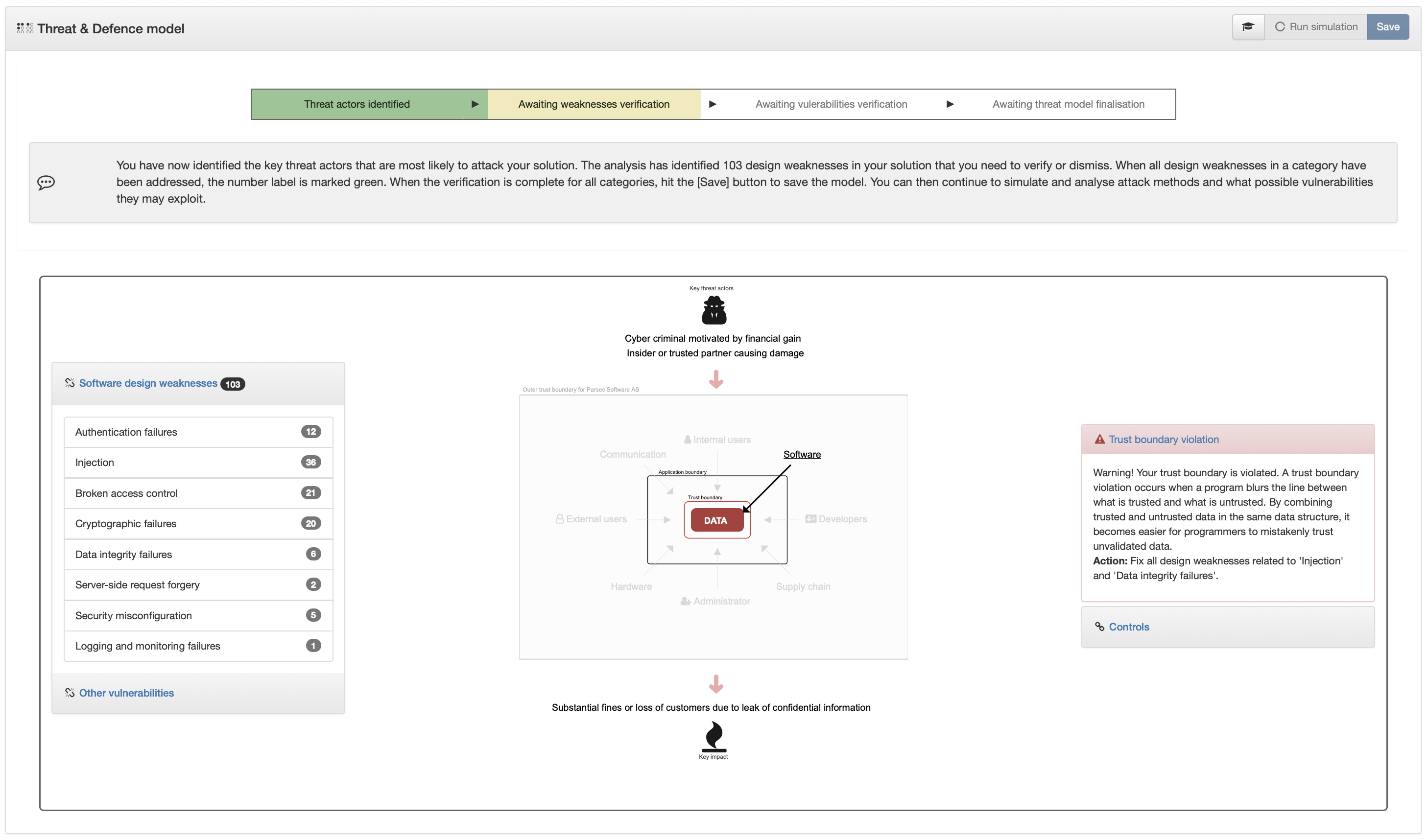
50%
After initial attack simulation where Design Weaknesses are identified
Risk Posture unlocked illustrating the risk posture in numbers
60%
After final attack simulation where Attack Methods and Additional Vulnerabilities are identified
70%
Overview of all relevant vulnerabilities that need to be addressed through mitigating Controls
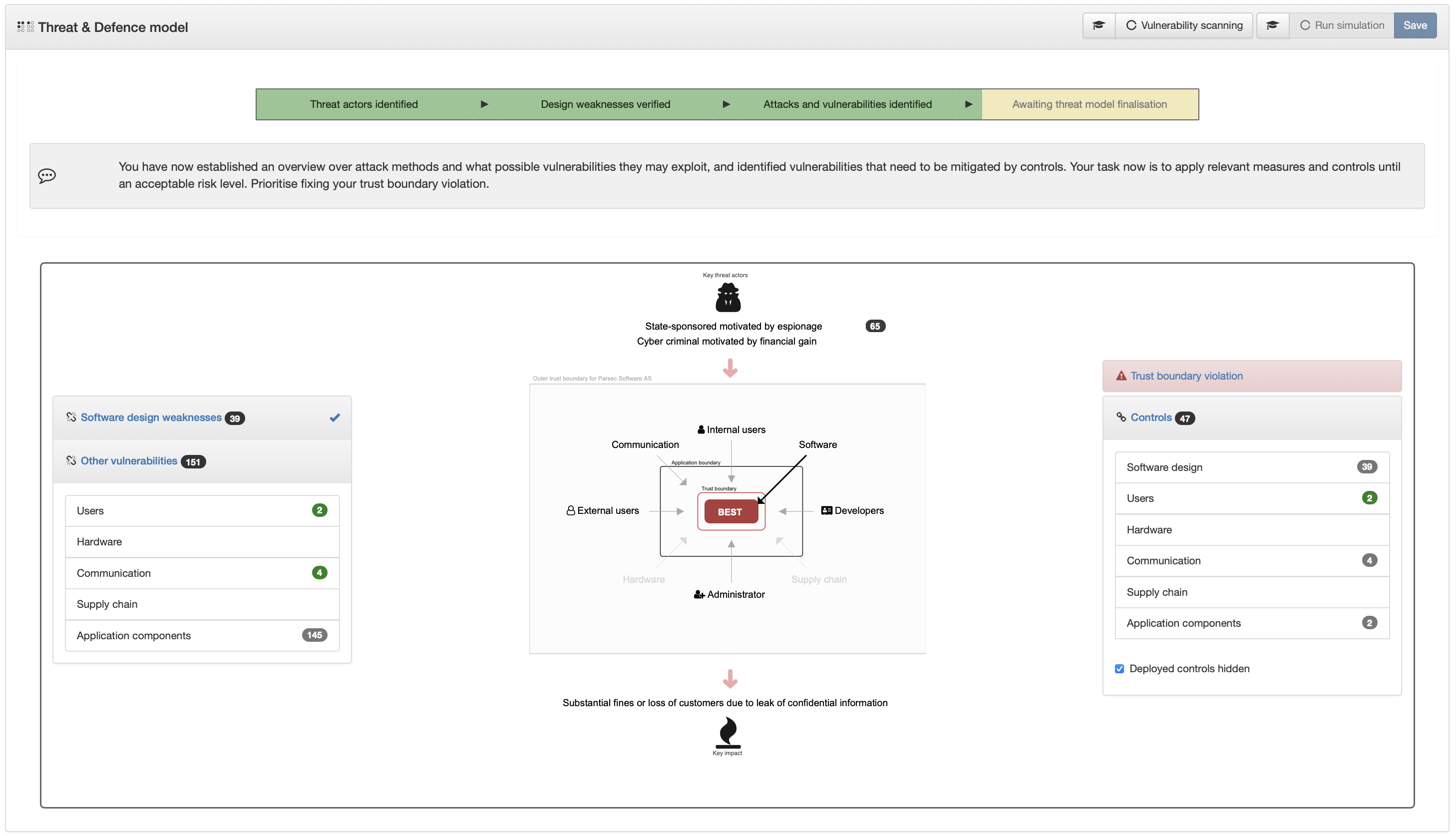
Vulnerability scanning of your application components unlocked.
80%
After assessing and deploying Controls causing trust boundary violation
90%
After assessing and deploying the majority of Controls
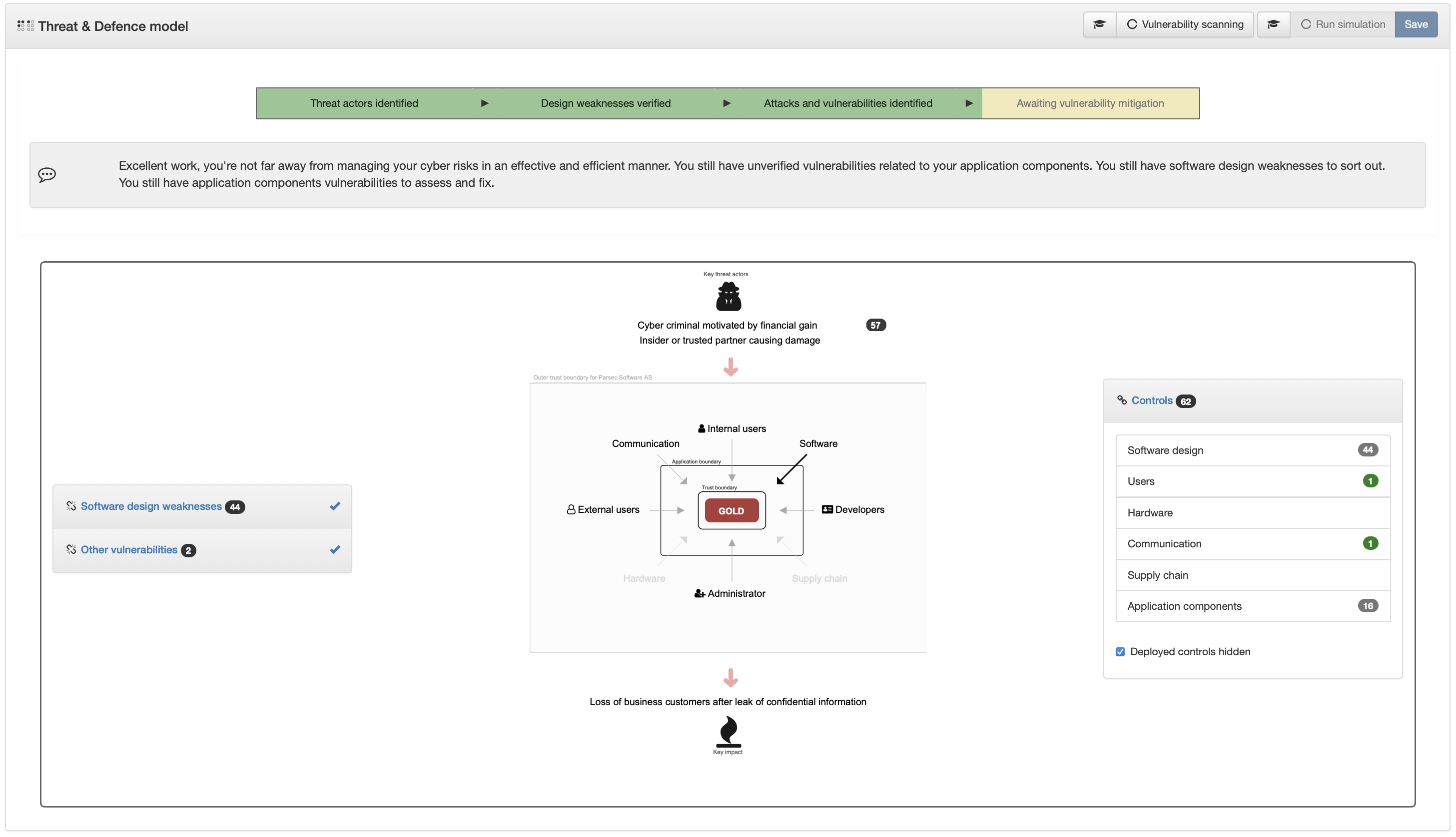
100%
Perfect equilibrium between risks and defence
YouTube CHANNEL
Visit our YouTube channel for our educational videos
Build your cyber security skills
If you're at a apprentice level, you'll find some great resources that will bring you up to speed on various cyber security and risk topics
In-depth how-to's
Understand important cyber risk topics in depth through educational videos
Tutorials for cyberriskguru.com
As a user of cyberriskguru.com, you'll find extensive tutorials that helps you with threat modelling, risk assessments and cyber strategy planning and execution
Subscribe
Hit the subscribe button in our channel to make sure your informed about new videos

